Exposing the BiG EVAL REST API to other Network Segments
Depending on your usage scenario it may be needed to expose the REST API of BiG EVAL to other network segments or even to the public internet to allow 3rd party services like Microsoft Power Automate to access the REST API.
Planning
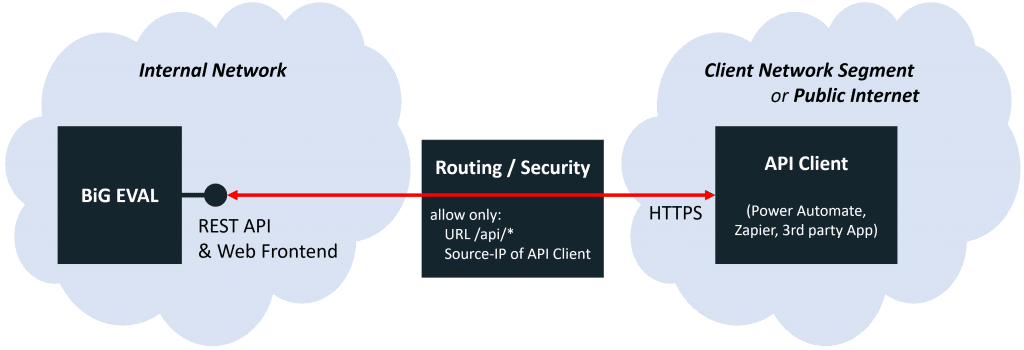
Your network infrastructure and architecture is very individual. So we cannot give you a common advice how to expose and secure the BiG EVAL REST API to other network segments or even the public internet. That’s why we suggest to sit down with your network architects and administrators to do the planning and implementation. In the following we show you some possibilities you should take in consideration.
Security Features of BiG EVAL
BiG EVAL comes with the following security features that allow you to harden and secure access to the BiG EVAL REST API.
- OAuth 2.0
All requests to the REST API are secured by OAuth 2.0 (access_code or client_security flows). This means, that all outside services need to be configured and permitted access by the BiG EVAL administrator. - SSL Communication
All HTTP communication can be encrypted with SSL-certificates. - Enforced user authentication
Access to the web frontend is secured either by BiG EVAL’s own user management or also via LDAP Single Sign on. - Logging
All HTTP-requests are logged for at least 5 days.
Network Security Infrastructure
Your network infrastructure almost certainly has some security appliances or technologies like:
- Firewalls
- Proxy Servers
- Application Security Appliances
- Traffic Analyzers
- and more
You network architects and administrators know best how to utilize these appliances correctly to first, expose the BiG EVAL REST API to another network segment, and second, to secure and limit access to the REST API.
What considerations you should take as well
- The web server of BiG EVAL serves the REST API as well as the Web Frontend of BiG EVAL. Both of these services are provided on the same host only separated by subfolders.
– REST API: https://bigeval.mycompany.com/api/v1/…
– Web-Frontend: https://bigeval.mycompany.com/
This means, that the web-frontend will be exposed to the other network segment or public internet as well if you don’t apply a filter on your firewall, proxy server or other security devices. - Use IP filtering features of your network security appliances to limit access to the REST API.
Implementation
These are the things that need to be done to expose the REST API of BiG EVAL to other network segments. Depending on your network infrastructure and security needs you may add other actions.
- Configure a DNS-name to be available in the other network segment or the public internet.
- Ensure BiG EVAL listens on that DNS-name by adding the URL to the appsettings.json and registering the URL in windows.
- Configure BiG EVAL to use HTTPS as the communication channel.
- Configure a device (proxy, firewall or similar) to route HTTPS-traffic between the BiG EVAL server and the other network segment or the public internet.
- Apply IP-filtering or similar features to limit the allowed traffic.
- Apply URL-filtering to allow access to the API only (/api/*).
- Add an API-client for your outside service that should access BiG EVAL.
